



Ethical Hacking Projects with Source Code" provides a comprehensive guide for anyone interested in mastering ethical hacking skills. These projects cover a wide range of practical scenarios, offering hands-on experience in identifying and fixing vulnerabilities across various systems and applications. From setting up a penetration testing lab and performing web application vulnerability assessments to simulating phishing attacks and conducting malware analysis, each project helps develop essential skills for aspiring ethical hackers.
The source code provided with each project serves as a valuable learning tool, allowing individuals to see real-world implementation and gain a deeper understanding of tools and techniques used in penetration testing, vulnerability scanning, and exploitation. These projects cater to both beginners and intermediate learners, offering practical challenges and real-time feedback on security practices.
Tools like Metasploit, Burp Suite, Kali Linux, Wireshark, and SQLMap are featured, allowing users to work with industry-standard software. Each project not only focuses on exploiting vulnerabilities but also emphasizes the importance of reporting findings and improving cybersecurity measures. Ultimately, these projects empower individuals to improve their skills, build a robust ethical hacking portfolio, and contribute to the ongoing battle against cyber threats.

Ethical hacking, also known as penetration testing or white-hat hacking, is the practice of intentionally probing systems, networks, or applications for vulnerabilities and weaknesses to help organizations strengthen their cybersecurity defenses.
Unlike malicious hackers, ethical hackers work with permission from the owner of the system or network and follow legal and ethical guidelines. The ultimate goal is to identify security flaws before malicious hackers (black-hat hackers) can exploit them.
These ethical hacking projects are essential for anyone looking to enhance their skills in cybersecurity and penetration testing. Each project focuses on different aspects of ethical hacking, ranging from web application security and network scanning to Wi-Fi cracking and social engineering. Tools like OWASP Juice Shop and Metasploit Framework allow you to practice exploiting vulnerabilities, while SQLMap and Nikto focus on scanning for SQL injection and web server weaknesses.
Kali Linux serves as a powerful OS with preloaded security tools. BeEF and SET are great for testing social engineering tactics, and tools like Wifite and Aircrack-ng specialize in wireless network security. Other projects like Responder and TheHarvester focus on network poisoning and open-source intelligence gathering. These tools, when used together, provide a comprehensive platform for ethical hackers to assess vulnerabilities and improve system security.
OWASP Juice Shop is a vulnerable web application designed for security testing. It simulates real-world security flaws, including SQL injection, cross-site scripting (XSS), and broken authentication.
The platform is designed to help developers, security enthusiasts, and penetration testers identify vulnerabilities in a controlled environment. It's a great tool for learning web application security practices.
Metasploit is an advanced penetration testing framework used to identify, exploit, and validate vulnerabilities in systems. It provides a set of tools for writing and testing exploits, delivering payloads, and simulating attacks. It is one of the most popular tools in ethical hacking, providing real-world insights into the security gaps of various systems.
SQLMap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities. It supports various database management systems, allowing ethical hackers to gain unauthorized access to databases and retrieve sensitive information. SQLMap also provides features like user enumeration and data exfiltration.
Sn1per is an automated penetration testing tool used for surveillance and vulnerability scanning. It performs a wide range of tests, including port scanning, vulnerability assessments, and web application security scans. It integrates with Metasploit for easy exploitation, making it an essential tool for ethical hackers.
Nmap (Network Mapper) is one of the most widely used open-source network scanning tools. It helps ethical hackers discover devices and services on a network, identify open ports, and perform vulnerability scans. Nmap is essential for network surveillance, providing valuable data for penetration testing.
Kali Linux is a Debian-based distribution built for digital forensics and penetration testing. It comes preloaded with hundreds of security tools for tasks like network scanning, vulnerability exploitation, and social engineering. It’s one of the most popular operating systems used by ethical hackers and penetration testers worldwide.
Beef is a powerful penetration testing tool that focuses on web browser vulnerabilities. It enables ethical hackers to exploit browser weaknesses and perform advanced attacks, such as cross-site scripting (XSS), to control the browser and gather sensitive information from users.
Wifite is a tool designed for automated Wi-Fi network cracking. It targets WEP and WPA/WPA2-PSK encryption and uses various attacks, including dictionary and brute-force methods, to crack network passwords. Ethical hackers use Wifite to test the security of wireless networks.
Empire is a post-exploitation framework that enables ethical hackers to deploy PowerShell and Python agents on compromised systems. It supports a variety of attack vectors, including credential dumping, lateral movement, and command-and-control communications, allowing hackers to maintain control over compromised systems.
Phishing Frenzy is a tool designed to create and execute phishing campaigns for penetration testing. It helps simulate social engineering attacks to test how vulnerable individuals or organizations are to phishing scams. It’s an effective tool for raising awareness about phishing threats.
Responder is a tool used for performing network poisoning attacks such as LLMNR, NBT-NS, and MDNS. It helps ethical hackers capture sensitive data, such as credentials, by impersonating network services and tricking machines into sending information to an attacker-controlled device.
The Harvester is an open-source intelligence-gathering tool that collects information from public sources, including search engines and social media platforms. It gathers email addresses, domain names, and other information useful for reconnaissance during penetration testing.
Nikto is a web server scanner that identifies security flaws in web servers. It performs comprehensive tests for outdated software, security misconfigurations, and potential vulnerabilities. Ethical hackers use Nikto to perform quick and thorough assessments of web application security.
Aircrack-ng is a suite of tools used for assessing Wi-Fi network security. It helps ethical hackers crack WEP and WPA/WPA2-PSK encryption, capture packets, and perform other attacks on wireless networks to identify weaknesses and improve security.
The Social-Engineer Toolkit is a powerful framework used to simulate social engineering attacks. It allows penetration testers to create phishing emails, credential harvesting forms, and perform various other social manipulation tactics to test human vulnerabilities in security.
These projects provide a hands-on approach to ethical hacking, offering valuable experience in penetration testing, network security, and exploit development.
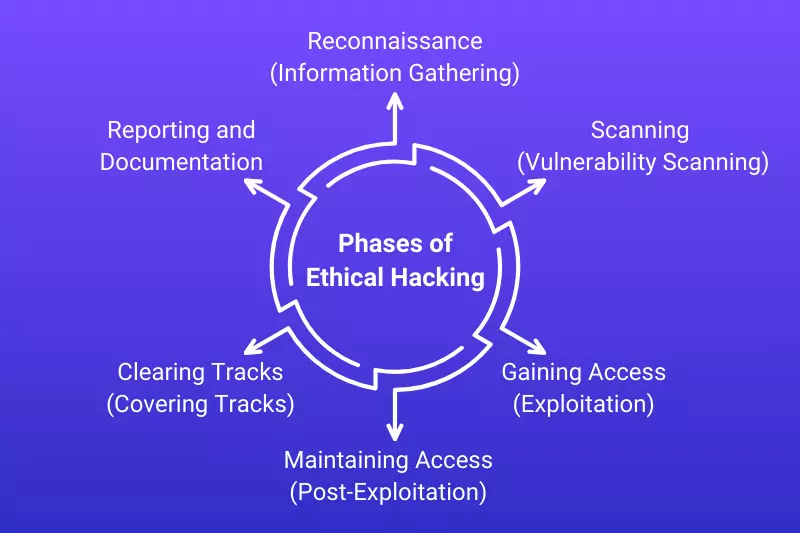
Ethical hacking, also known as penetration testing or white hat hacking, follows a structured process to identify vulnerabilities and weaknesses in a system, network, or application. The process is divided into several phases to ensure a thorough evaluation of the system's security. Below are the key phases of ethical hacking, explained in detail:
The first step involves gathering as much information as possible about the target system, which can help in identifying potential vulnerabilities.
Types of Reconnaissance:
Tools:
In this phase, ethical hackers look for open ports, services, and potential vulnerabilities in the target system. It involves identifying which services or devices are accessible and understanding the nature of the potential weaknesses.
Techniques:
Tools:
This phase is where the ethical hacker attempts to exploit the vulnerabilities found during the scanning phase. The goal is to gain unauthorized access to the system in order to demonstrate how a malicious hacker could exploit those weaknesses.
Exploitation Techniques:
Tools:
Once access to the system has been gained, the ethical hacker tries to maintain persistent access to demonstrate the potential impact of a real attack. This allows the hacker to maintain control over the system even if the initial vulnerability is patched.
Techniques:
Tools:
After accessing and potentially manipulating a system, the ethical hacker’s responsibility is to ensure that all traces of their actions are erased. This step simulates the behavior of malicious hackers who attempt to hide their tracks to avoid detection.
Techniques:
Tools:
The final phase involves compiling a comprehensive report detailing the findings, including the vulnerabilities discovered, exploitation methods used, and recommendations for fixing or mitigating the issues.
Components of the Report:
Tools:

Ethical hacking projects provide a robust foundation for learning and practicing cybersecurity techniques. Each project focuses on a unique aspect of ethical hacking, from penetration testing and vulnerability scanning to social engineering and Wi-Fi security.
By exploring these tools and frameworks, ethical hackers can sharpen their skills, identify weaknesses in systems, and enhance the overall security posture of networks and applications. Whether you're a beginner or an experienced professional, these projects offer valuable insights and hands-on experience to help you stay ahead in the ever-evolving field of cybersecurity.
Copy and paste below code to page Head section
Ethical hacking involves testing systems, networks, and applications to identify vulnerabilities and weaknesses before malicious hackers can exploit them. It helps improve security by proactively finding and addressing potential threats.
Ethical hacking projects provide practical, hands-on experience in identifying and exploiting vulnerabilities. Working on these projects helps improve your technical skills and prepares you for real-world penetration testing and cybersecurity roles.
Common tools include Metasploit, Nmap, Kali Linux, SQLMap, BeEF, Burp Suite, Wireshark, Aircrack-ng, and more. Each tool focuses on different aspects of ethical hacking, such as network scanning, vulnerability exploitation, or web application testing.
Yes, most ethical hacking tools are open-source and free to use for learning purposes. However, always ensure you're conducting tests on systems that you have explicit permission to access, as unauthorized testing can be illegal.
Start by understanding basic cybersecurity concepts, followed by learning how to use tools like Kali Linux and Metasploit. You can then move on to ethical hacking projects, such as setting up vulnerable environments like OWASP Juice Shop or participating in Capture The Flag (CTF) challenges.
Many of the projects listed, such as OWASP Juice Shop and TheHarvester, are beginner-friendly and designed to help you learn basic hacking techniques. However, some tools like Metasploit may require a deeper understanding of security concepts.

